Fun Tips About How To Protect Phi

A good way to keep phi data secure is to invest in enhanced encryption.
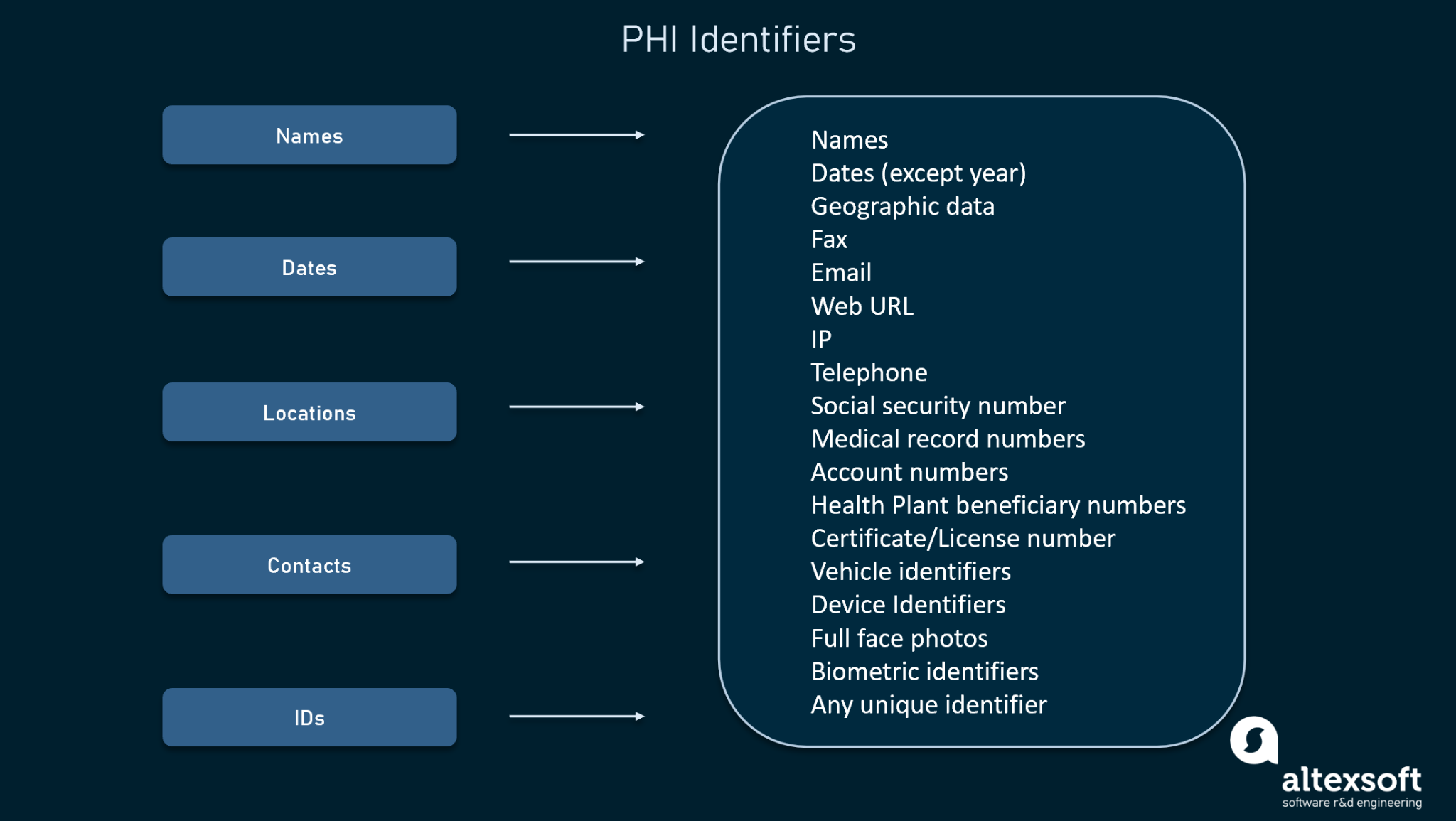
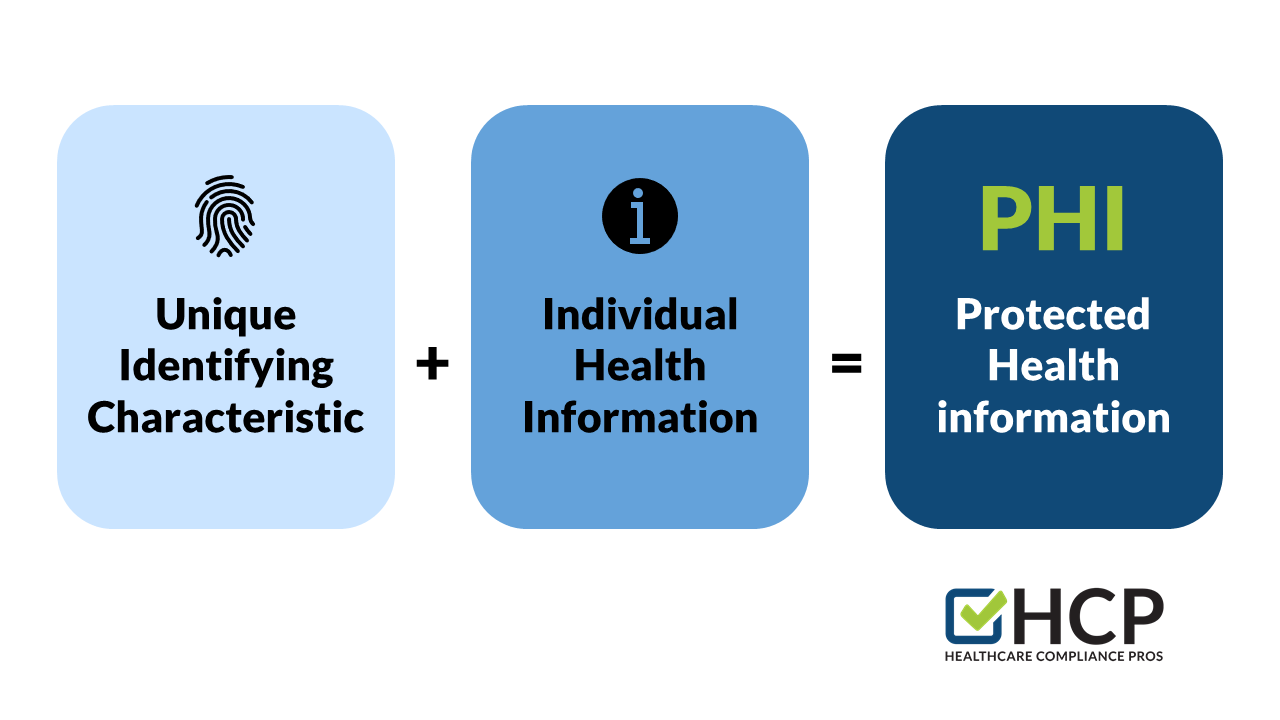
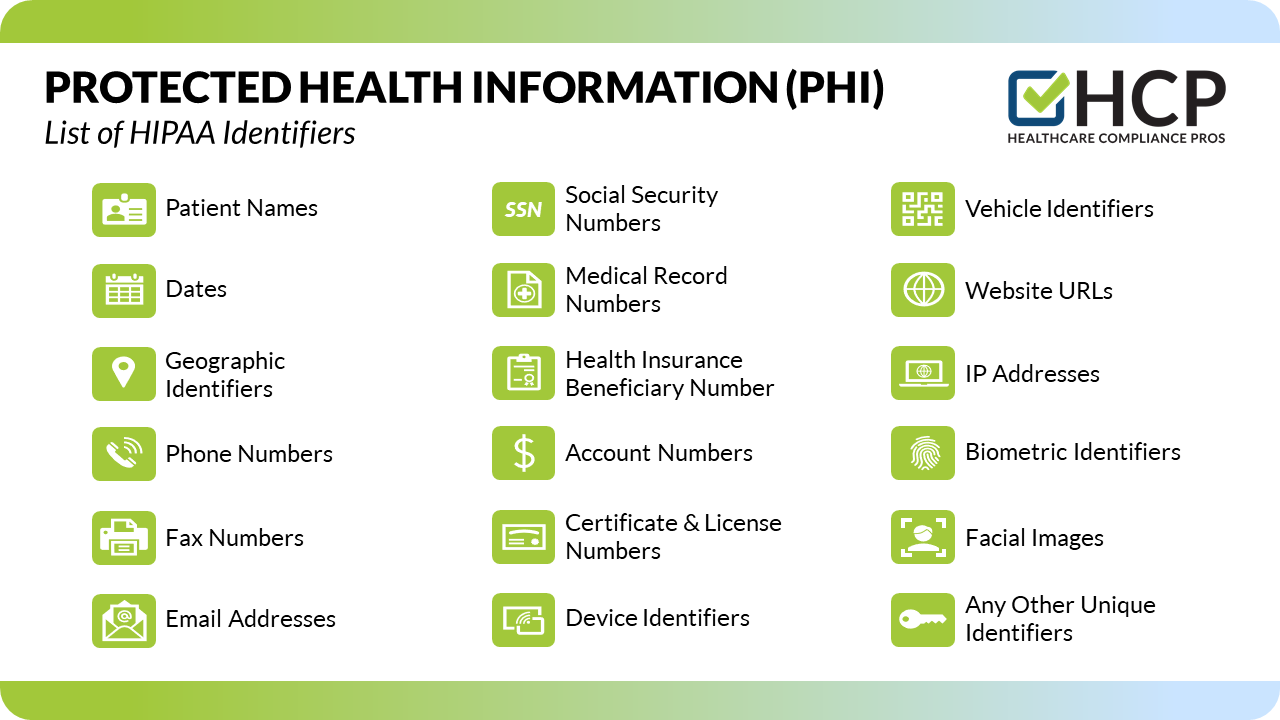
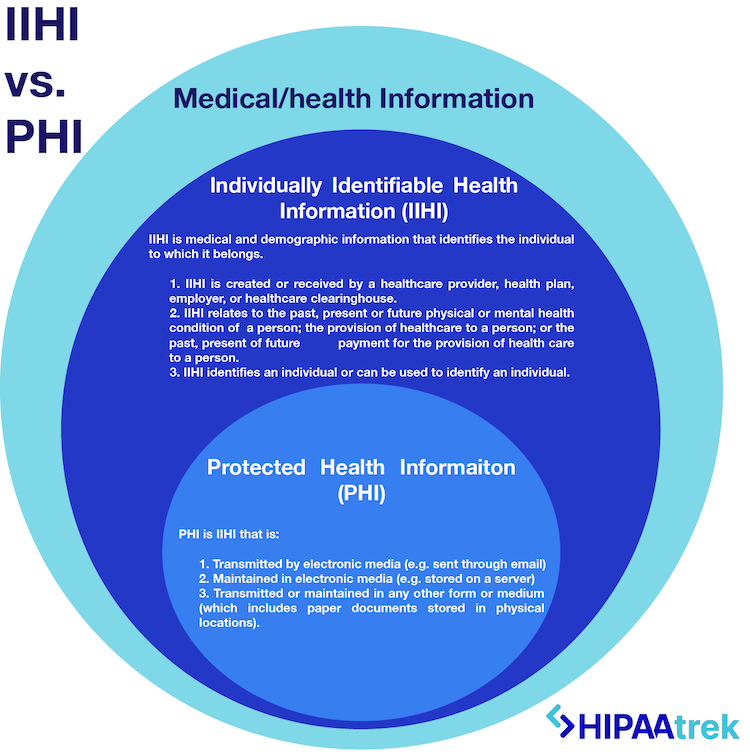
How to protect phi. Encryption is well known by security pros for preventing. Hipaa technical safeguards protect phi and are a major part of any hipaa security program. Examples of how to keep phi secure:
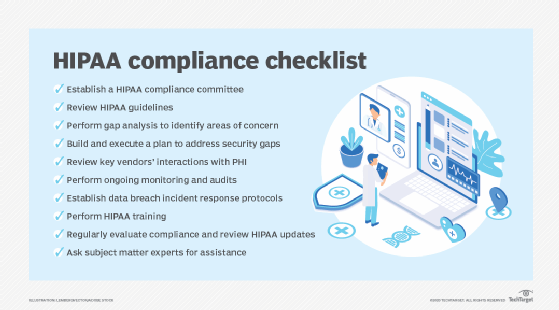
In part 2 of our hipaa security series we tackle the basic steps to protect phi through physical safeguards. Produce formal documented policy and procedures for phi use, disclosure, and disposal. With tokenization and encryption, your identifiable data can be made.
Create a bring your own device (byod) agreement, with clear usage rules for employees. Use only encrypted methods when sending phi electronically. If phi is in a place where patients or others can see it, cover or move it if you work with phi on your desk or on a computer, make sure no one can walk up.
Business associate agreements can be tailored to each situation, but should always include key legal language to meet the standards set by regulators. Covered entities can also require employees. Here are the top 25 tips for protecting pii that provide some strategies for mitigating the risk of data loss and leakage.
When phi is used or accessed, the safeguards that protect it must. Use a privacy screen to prevent people close by from. Using cybersecurity to protect ephi is a key feature of hipaa.
Comply with the hipaa security rule. Train employees in ephi handling implement encryption and. Healthcare organizations can use these phive steps now to make a business case for protecting phi: